An Active Jammer-based Adversarial Attack Method Against SAR Automatic Target Recognition
-
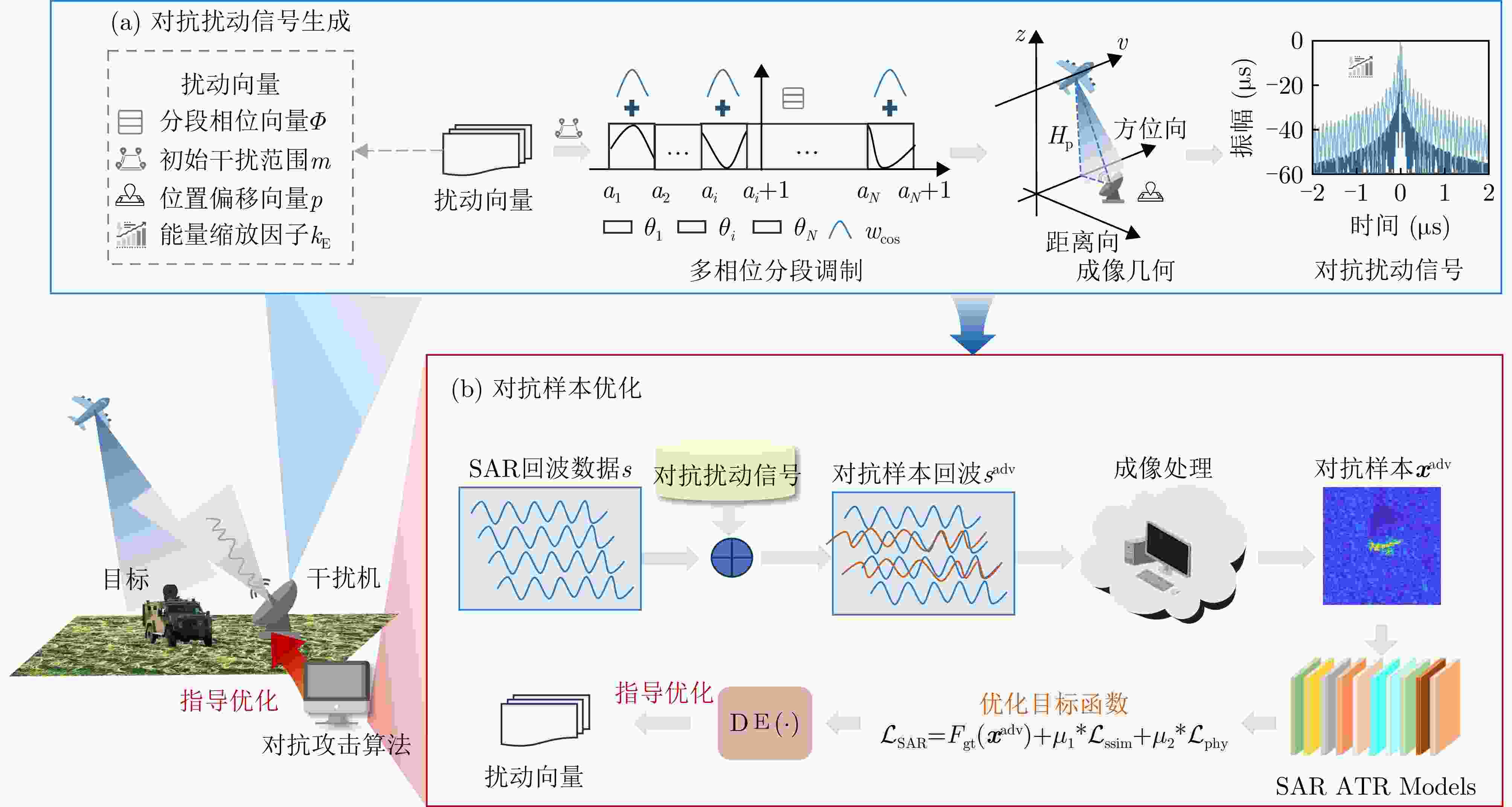
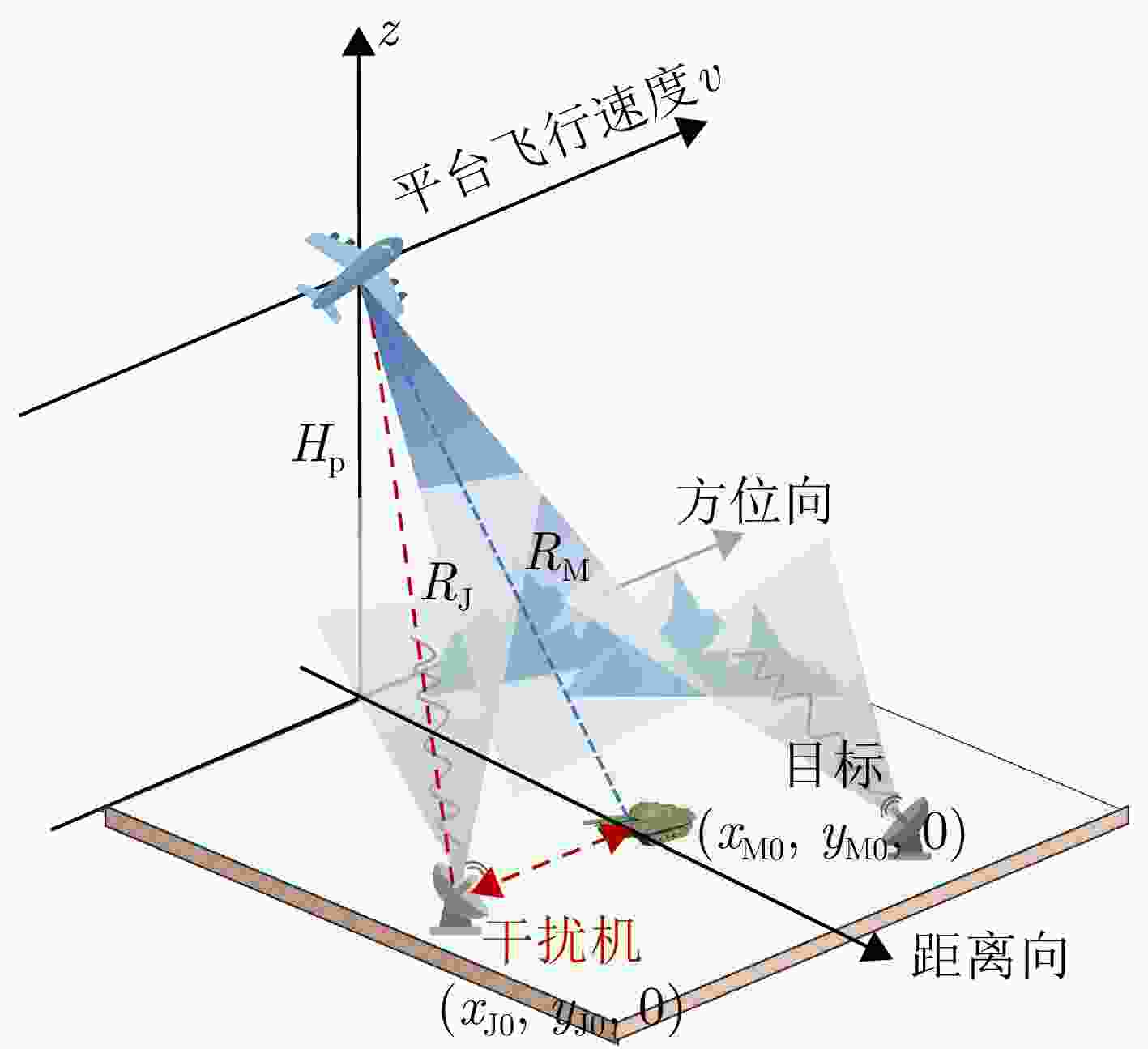
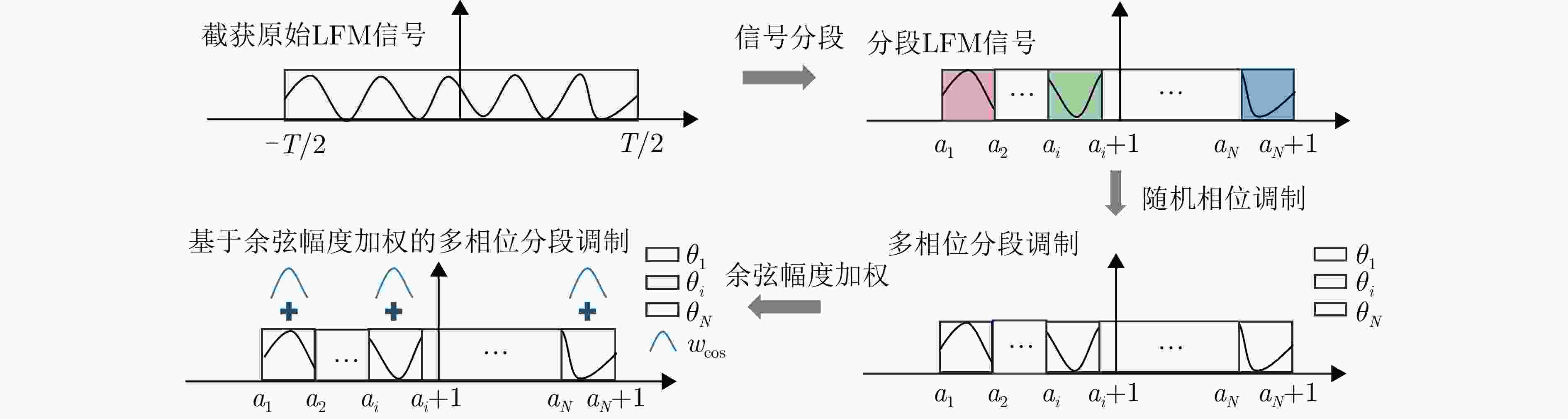
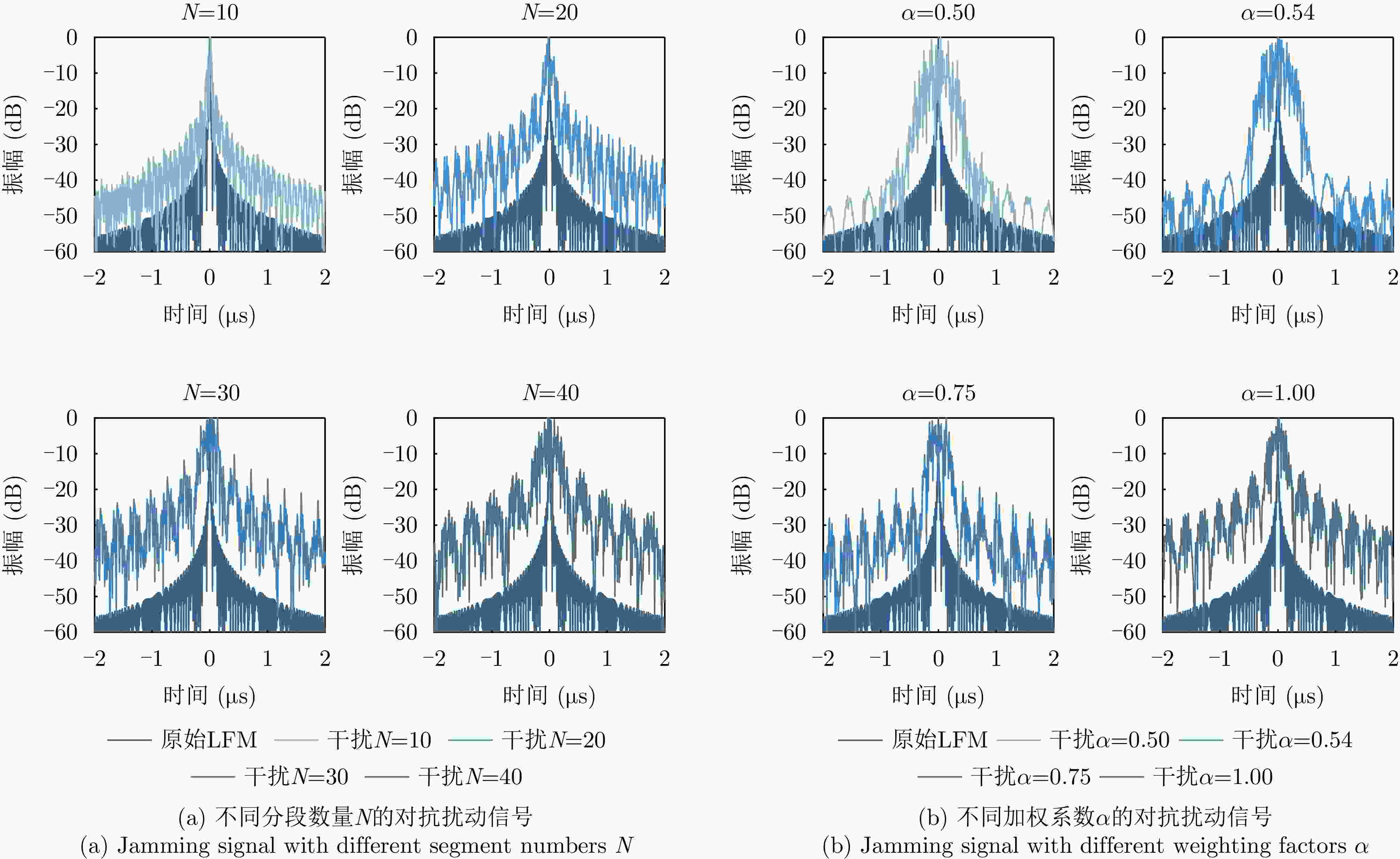
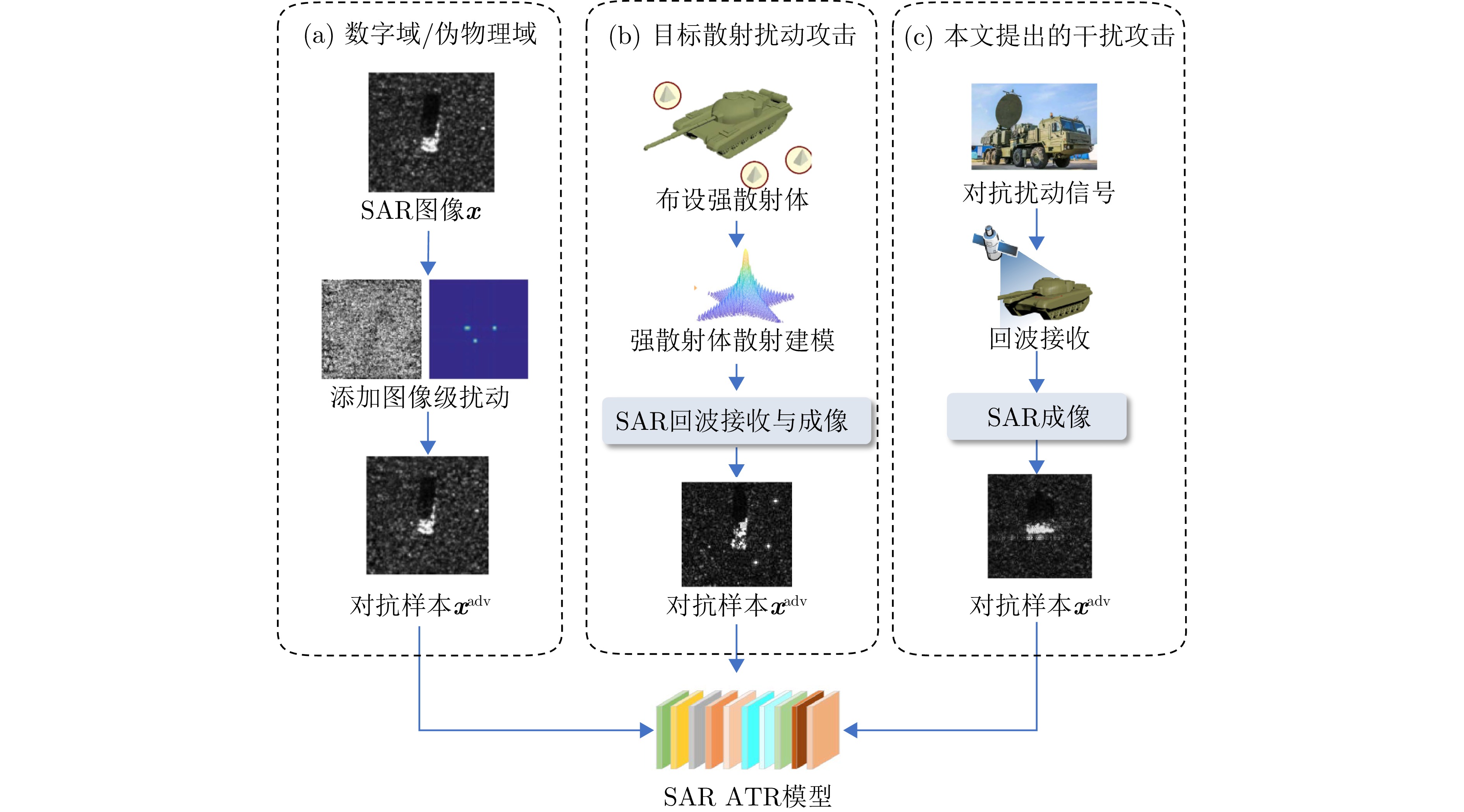
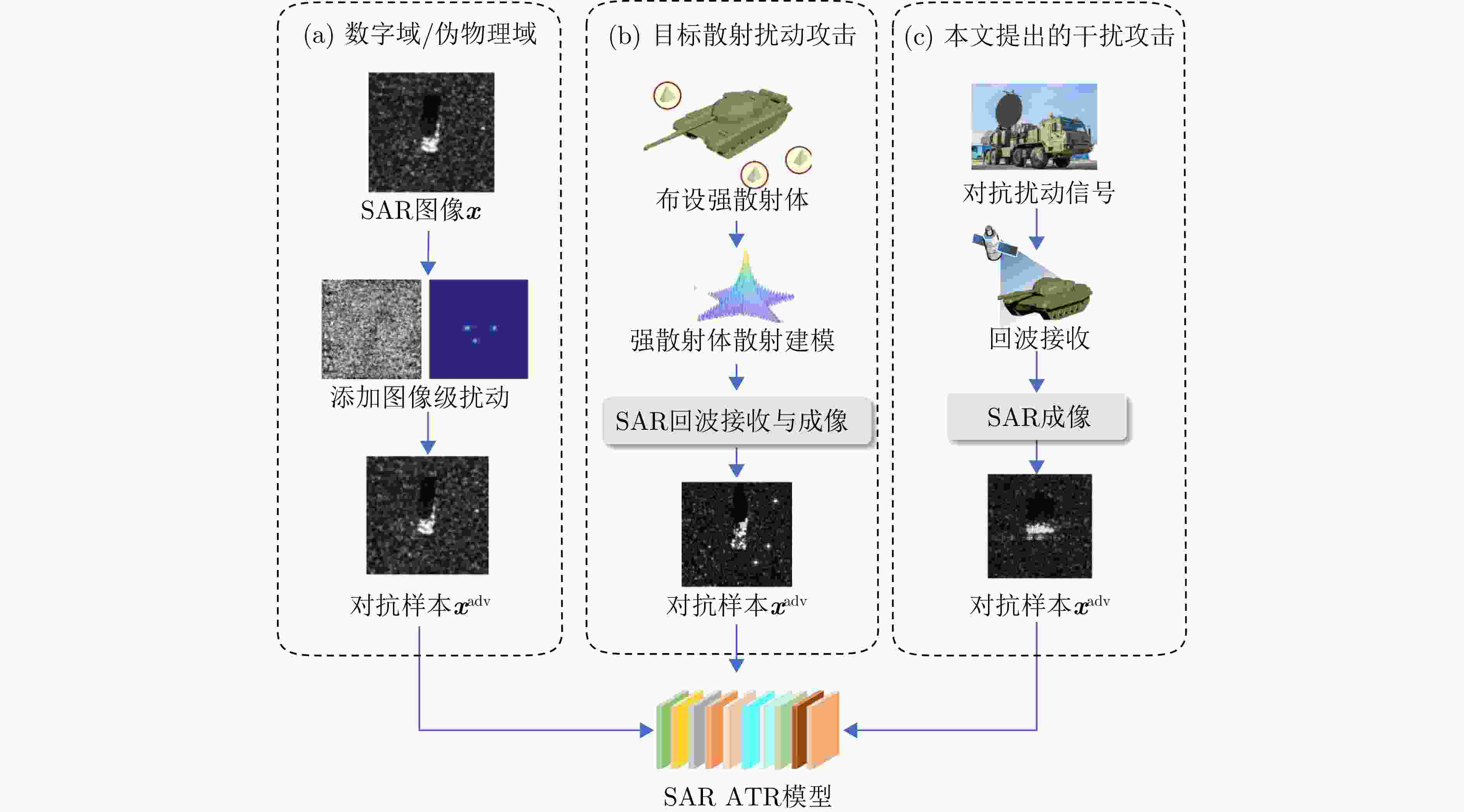
摘要: 合理利用SAR对抗样本可以使得特定目标在智能探测技术下实现遥感隐身,从而避免被敌方探测或识别。数字域的SAR对抗方法仅在图像域进行攻击,缺乏物理可实现性,现有物理域对抗方法通过在目标周围布置角反射器、超表面,借助电磁计算模拟对抗样本,但由于散射估计精度低,实际保护效能受限。为解决上述问题,该文将SAR有源干扰技术与对抗攻击方法相结合,提出了基于有源干扰机的SAR智能识别对抗方法,在信号域扰动目标回波信号以生成对抗样本。首先,选择基于余弦幅度加权的多相位分段调制干扰技术,通过扰动分量的设计,实现对抗扰动信号的参数化控制;然后,基于SAR成像链路,将有源干扰机生成的对抗扰动信号与目标的回波信号融合,经成像处理得到具有物理意义的SAR对抗样本;最后,引入差分进化算法,动态调整多相位分段调制干扰的能量分布与空间覆盖范围等参数,进而优化SAR对抗样本,在干扰强度较小的情况下取得最佳攻击成功率。实验结果表明,所提方法在MSTAR数据集上实现平均90.88%的攻击成功率,并对5种SAR ATR模型具有较强的可转移性,其中最高可达75.57%。该方法实现了更具物理可实现性的对抗样本生成,为遥感探测中特定目标的安全防护开辟新的解决思路,并为真实场景下有源干扰信号的应用提供智能化指导。Abstract: The effective utilization of Synthetic Aperture Radar (SAR) adversarial examples enables specific targets to achieve remote sensing stealth against intelligent detection systems, thereby evading detection and recognition by adversaries. Digital domain SAR adversarial methods, which operate exclusively in the image domain, produce adversarial images that are not physically realizable and therefore cannot generated by real SAR imaging systems. Existing physical domain approaches typically involve deploying corner reflectors or electromagnetic metasurfaces around targets and simulating adversarial examples using via computational electromagnetics. However, the limited accuracy of scattering estimation often constrains the practical protective efficacy of these methods. To overcome these limitations, this paper proposes an active jammer-based adversarial attack method that integrates SAR active jamming technology with adversarial attack methods to generate adversarial examples by perturbing the target’s echo signals in the signal domain. First, a multiple-phase sectionalized modulation jamming method based on cosine amplitude weighting is selected, enabling parameterized control of the adversarial jamming signal through the design of perturbation components. Next, the adversarial jamming signal generated by the active jammer is fused with the target’s echo signal according to the principles and actual processes of SAR imaging and is then subjected to imaging processing to produce physically realizable SAR adversarial examples. Finally, the differential evolution algorithm is employed to dynamically adjust parameters, such as the energy distribution and jamming range of the adversarial jamming signal, thereby optimizing the SAR adversarial examples to achieve optimal attack success rates even with minimal interference intensity. Experimental results on the MSTAR dataset, a widely used benchmark in the field of SAR Automatic Target Recognition (ATR), show that the proposed method achieves an average fooling rate of 90.88% and demonstrates superior transferability across five different SAR ATR models, with the highest transfer fooling rate reaching 75.57%. Overall, the proposed method generates more physically realizable adversarial examples compared with existing digital domain methods, effectively protecting specific targets in remote sensing detection and providing guidance for the practical application of active jamming signals in real-world scenarios.
-
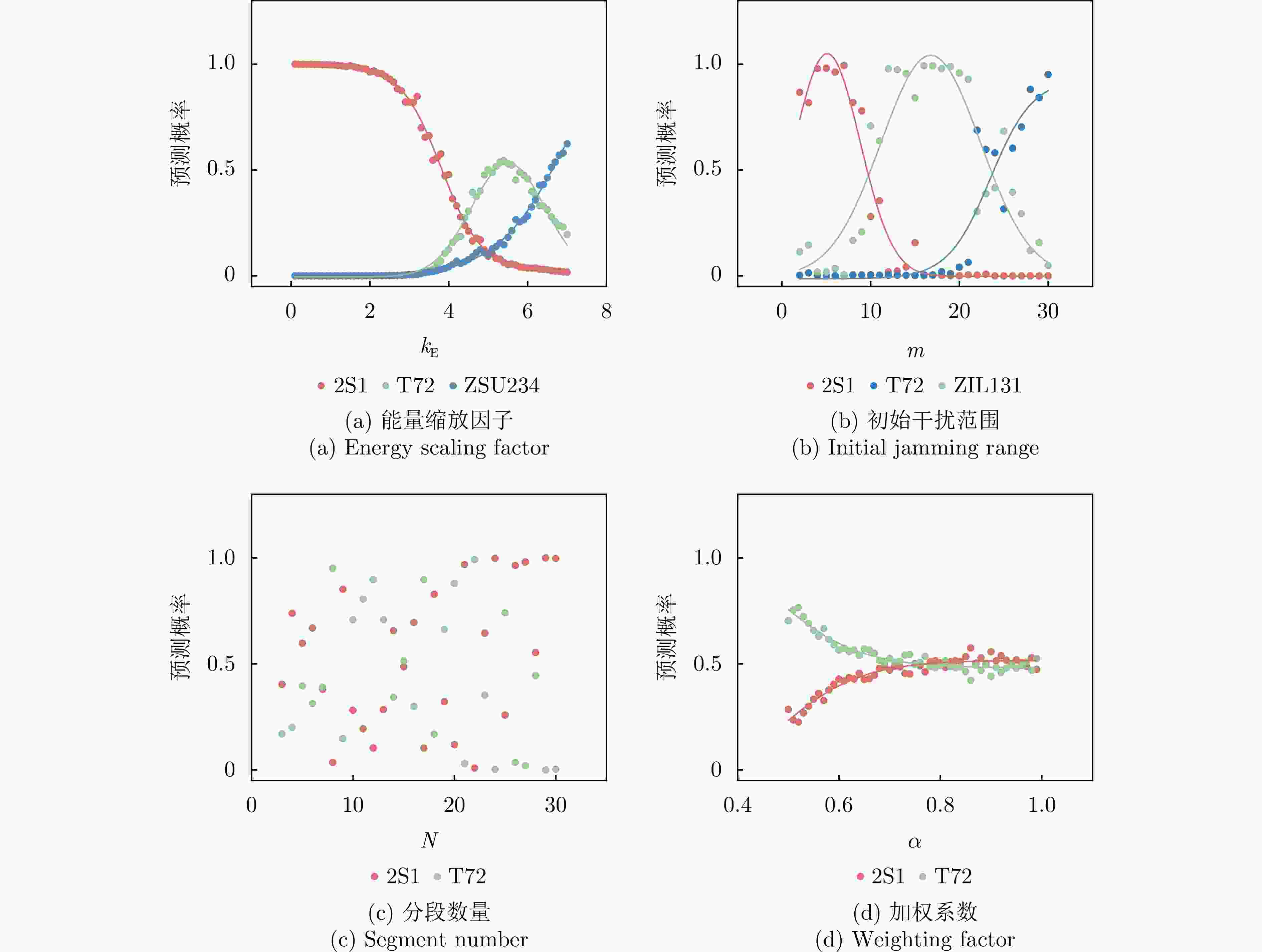
1 基于有源干扰机的SAR智能识别对抗方法算法
1. Jammer-based adversarial attack algorithm
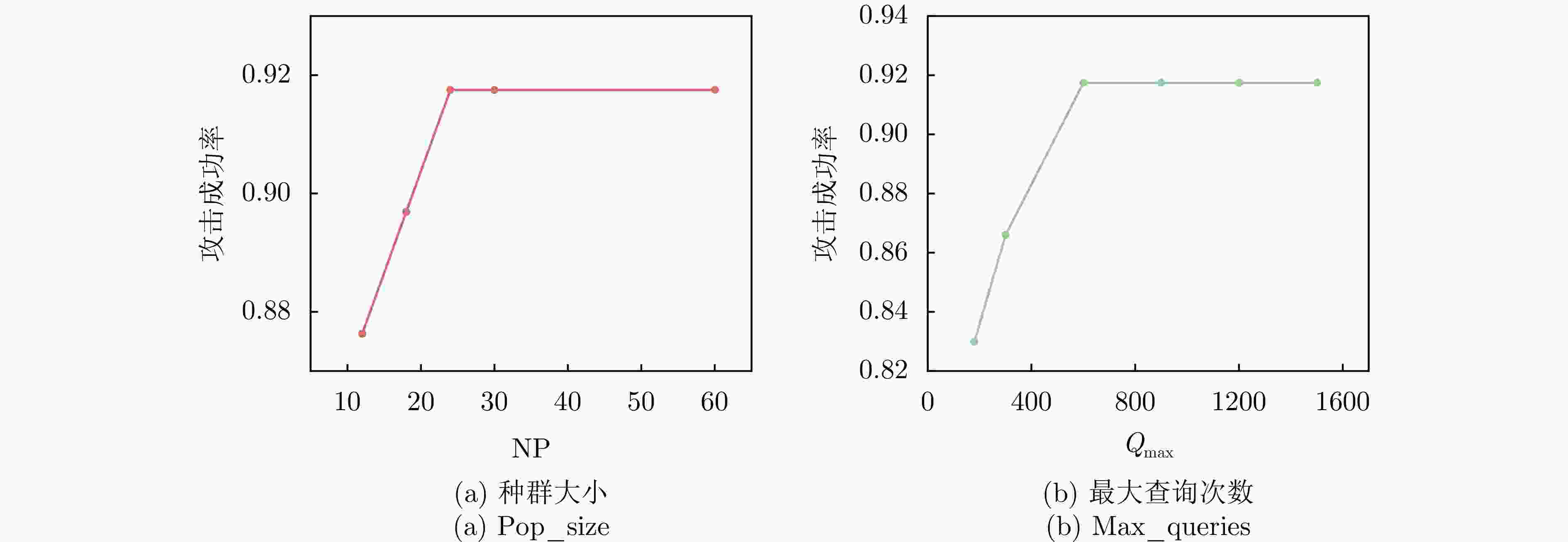
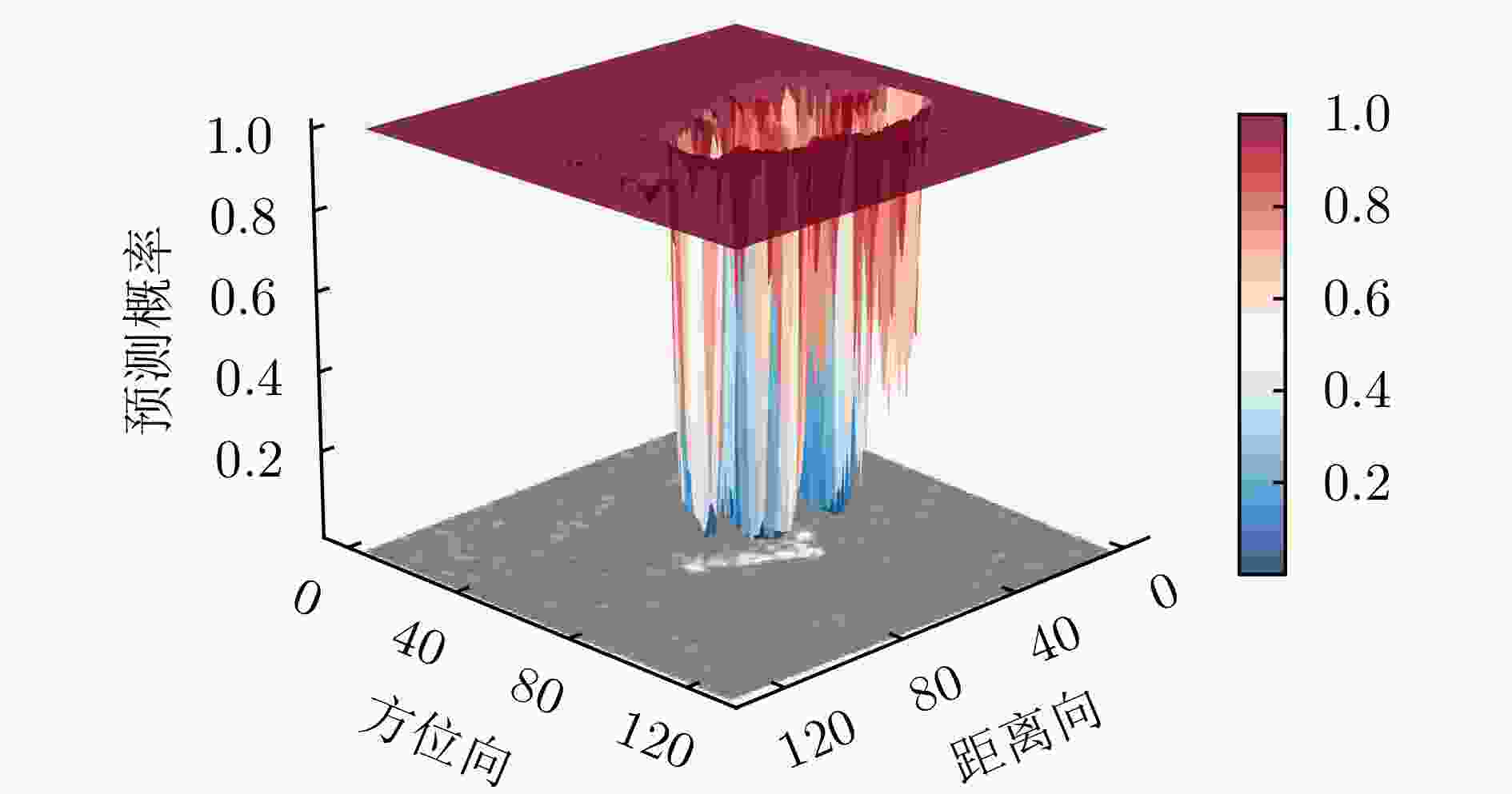
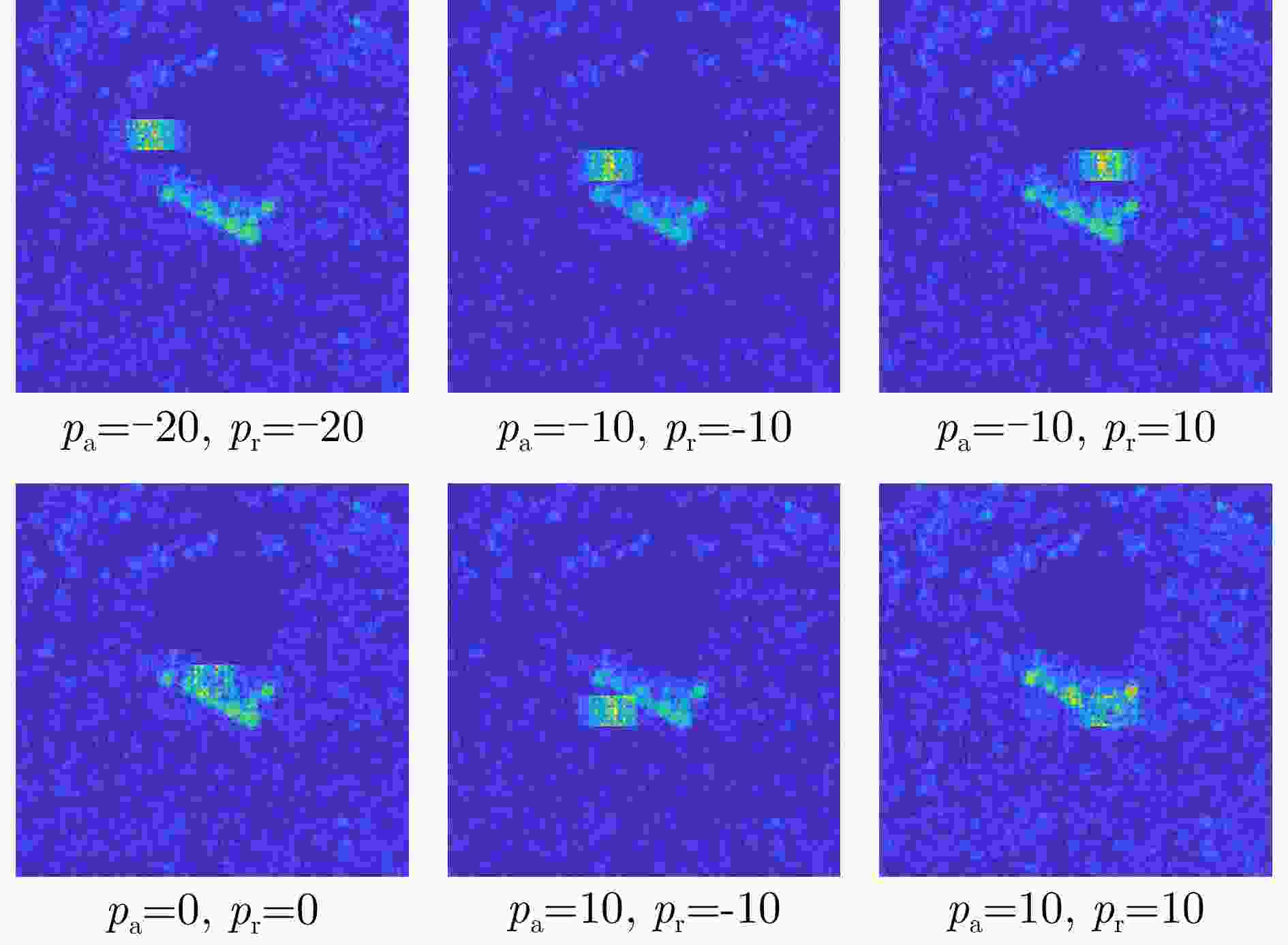
输入:原始SAR图像样本x及其标签$ y^{\mathrm{gt}} $,目标SAR系统成像参数$ \varTheta $,分类网络F,扰动向量范围$ \left[{\boldsymbol{r}}_{\text {min }},{\boldsymbol{ r}}_{\text {max }}\right] $,DE算法的种群大小NP和最
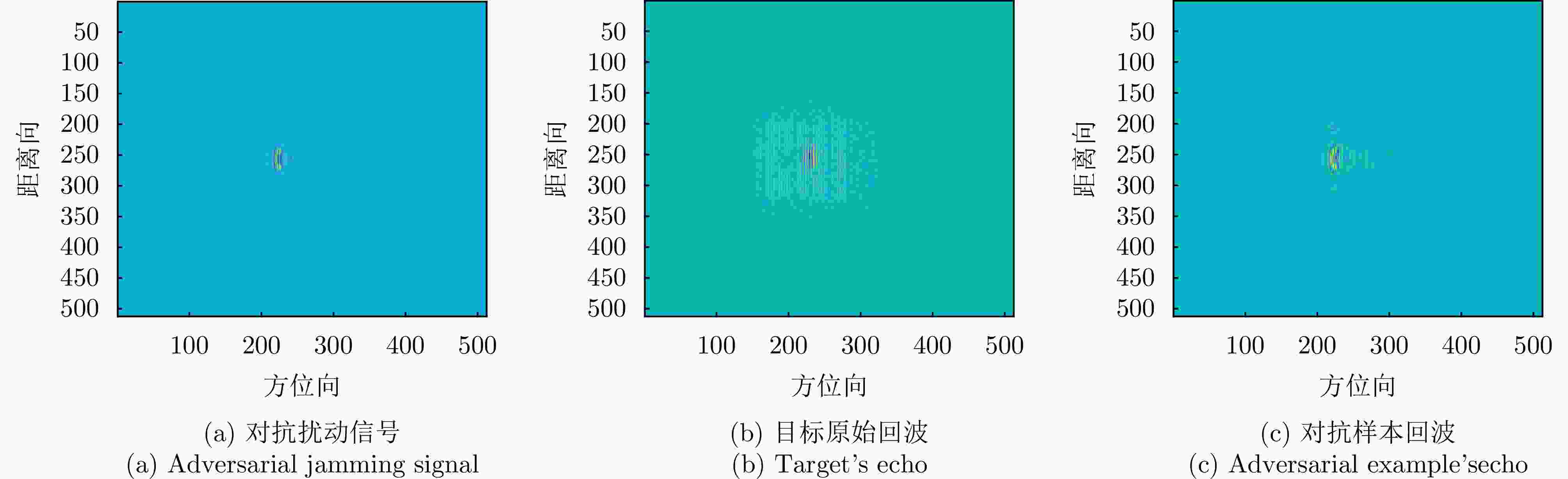
大查询次数$ Q_{\max } $输出:对抗样本$ {\boldsymbol{x}}^{{\mathrm{adv}}} $ 1. 直接输入原始样本的回波信号$ s(t, \tau) $或通过式(20)计算原始SAR图像样本的回波信号$ s(t, \tau) $ 2. 设置当前代数G=1,初始化种群得到NP个候选解$ {\boldsymbol{r}}_{0}^{G}=\left[{\boldsymbol{r}}_{1}^{G}, {\boldsymbol{r}}_{2}^{G}, \cdots, {\boldsymbol{r}}_{\mathrm{NP}}^{G}\right] $ 3. WHILE G$* $NP<$ Q_{\max } $ 4. 通过式(18)计算候选解对应的对抗扰动信号$ \left[ \varepsilon _{1}^{G}, \varepsilon_{2}^{G}, \cdots, \varepsilon_{\mathbb{NP}}^{G}\right] $ 5. 通过式(19)计算对抗样本回波并成像得到候选对抗样本$ \left[{\boldsymbol{x}}_{1}^{G}, {\boldsymbol{x}}_{2}^{G}, \cdots, {\boldsymbol{x}}_{{\mathrm{NP}}}^{G}\right] $ 6. 计算每个候选对抗样本的预测标签$ \left[\hat{y}_{1}^{G}, \hat{y}_{2}^{G}, \cdots, \hat{y}_{\mathrm{NP}}^{G}\right] $及目标函数值$ \left[\mathcal{L}_{1}^{G}, \mathcal{L}_{2}^{G}, \cdots, \mathcal{L}_{\mathrm{NP}}^{G}\right] $ 7. FOR j=1:NP 8. IF $ \hat{y}_{j}^{G}\ne y^{{\mathrm{gt}}} $ 9. 攻击成功,算法终止,输出最优解 10. ELSE 执行选择操作,返回当前最优解,进入步骤12作为新的个体 11. END 12. G=G+1 13. 对种群中个体执行变异和交叉操作得到候选解$ {\boldsymbol{r}}^{G} $ 14. END 15. 输出结果 表 1 MSTAR详细信息
Table 1. MSTAR dataset details
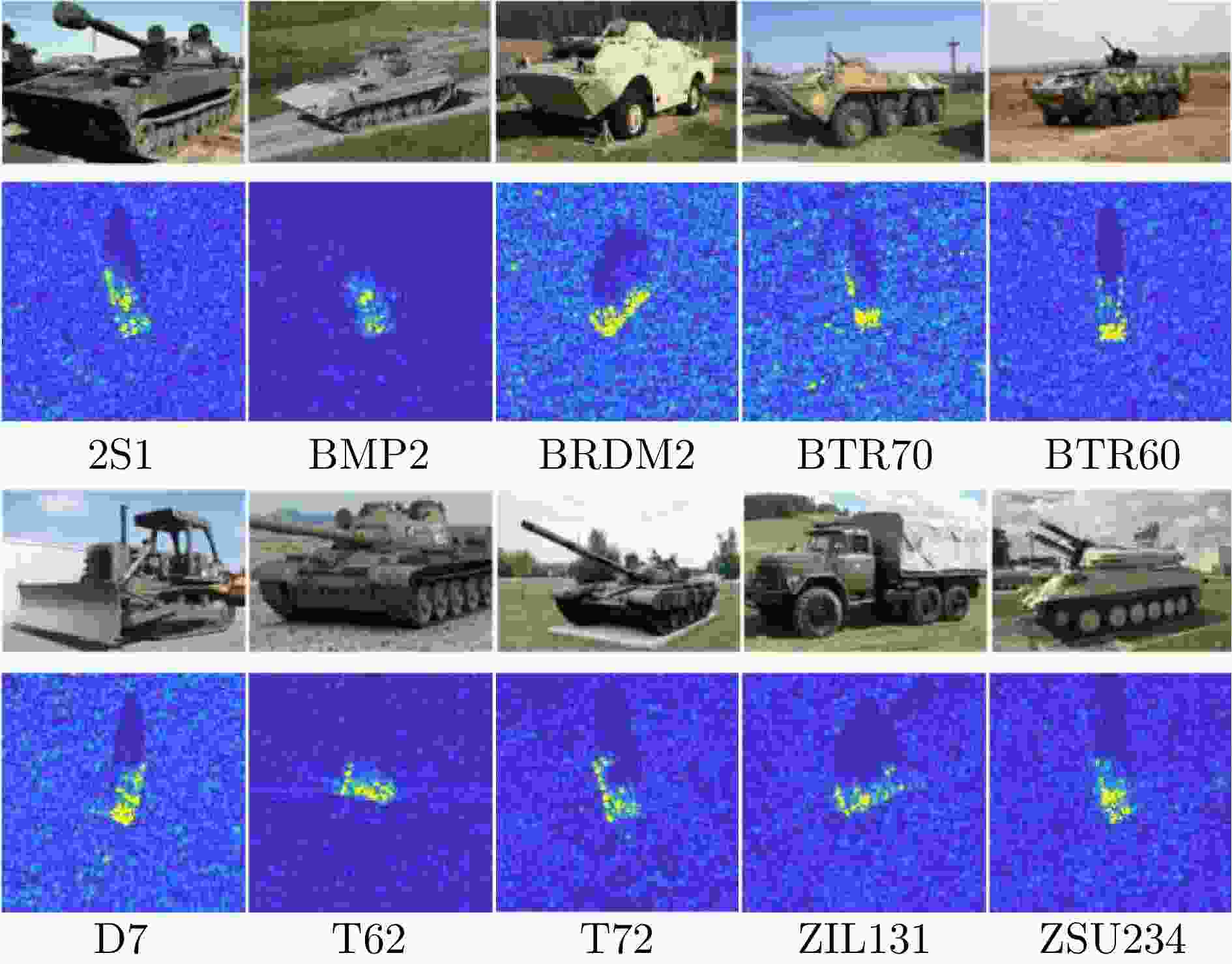
标签 类别名 训练集 测试集 0 2S1 299 274 1 BRDM2 298 274 2 BTR60 256 195 3 D7 299 274 4 T62 299 273 5 ZIL131 299 274 6 ZSU234 299 274 7 BMP2 233 195 8 BTR70 233 196 9 T72 232 196 总数 — 2747 2425 表 2 SAR ATR模型的训练结果(%)
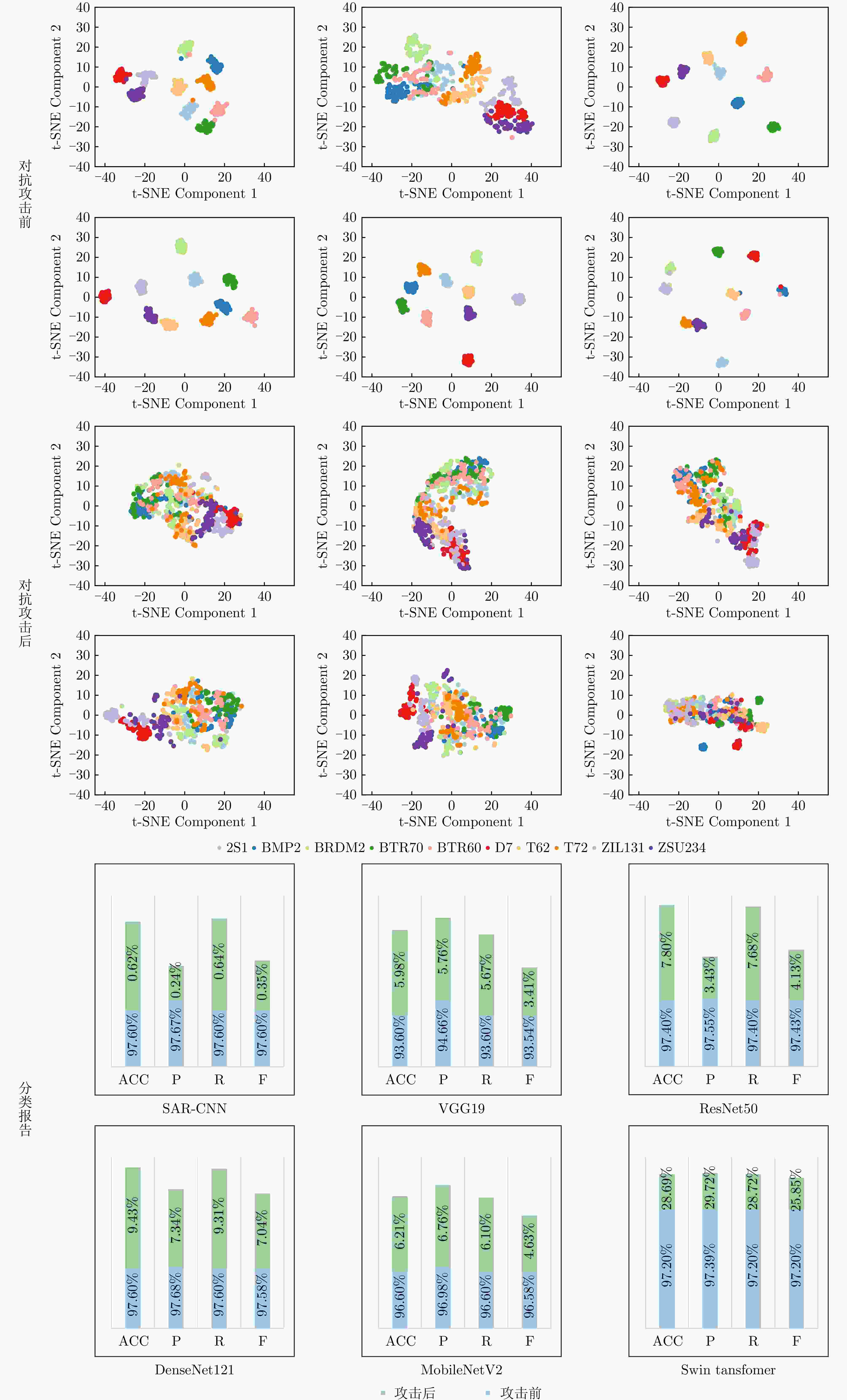
Table 2. Training and testing accuracy of six SAR ATR models (%)
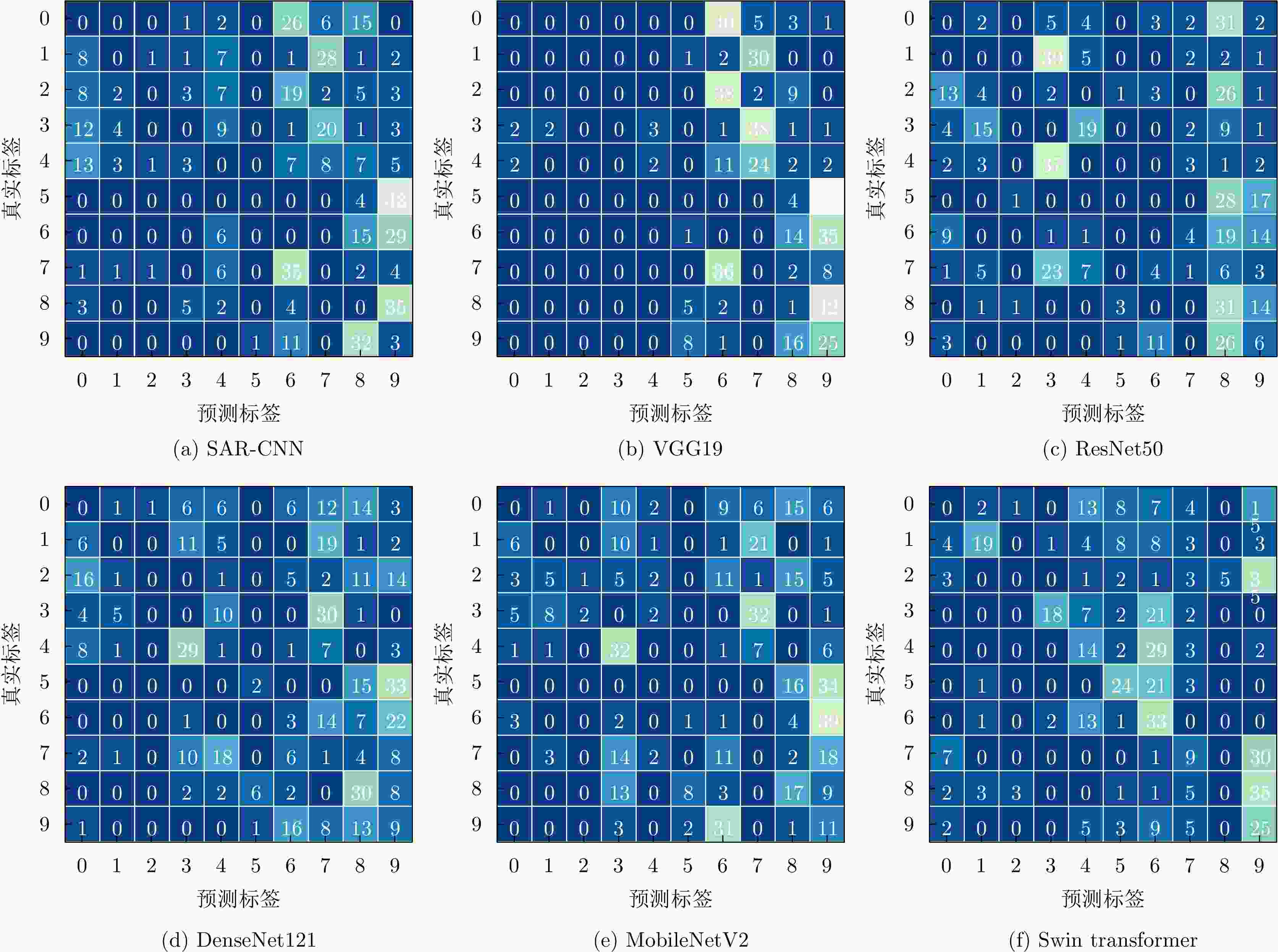
SAR目标识别网络 训练精度 测试精度 SAR-CNN 100 97.60 VGG19 99.64 93.60 DenseNet121 100 97.60 ResNet50 100 97.40 MobileNetV2 100 96.60 Swin transformer 100 97.20 表 3 不同对抗攻击方法对识别模型的攻击成功率(%)
Table 3. Fooling rate of different adversarial attack methods on SAR ATR Models (%)
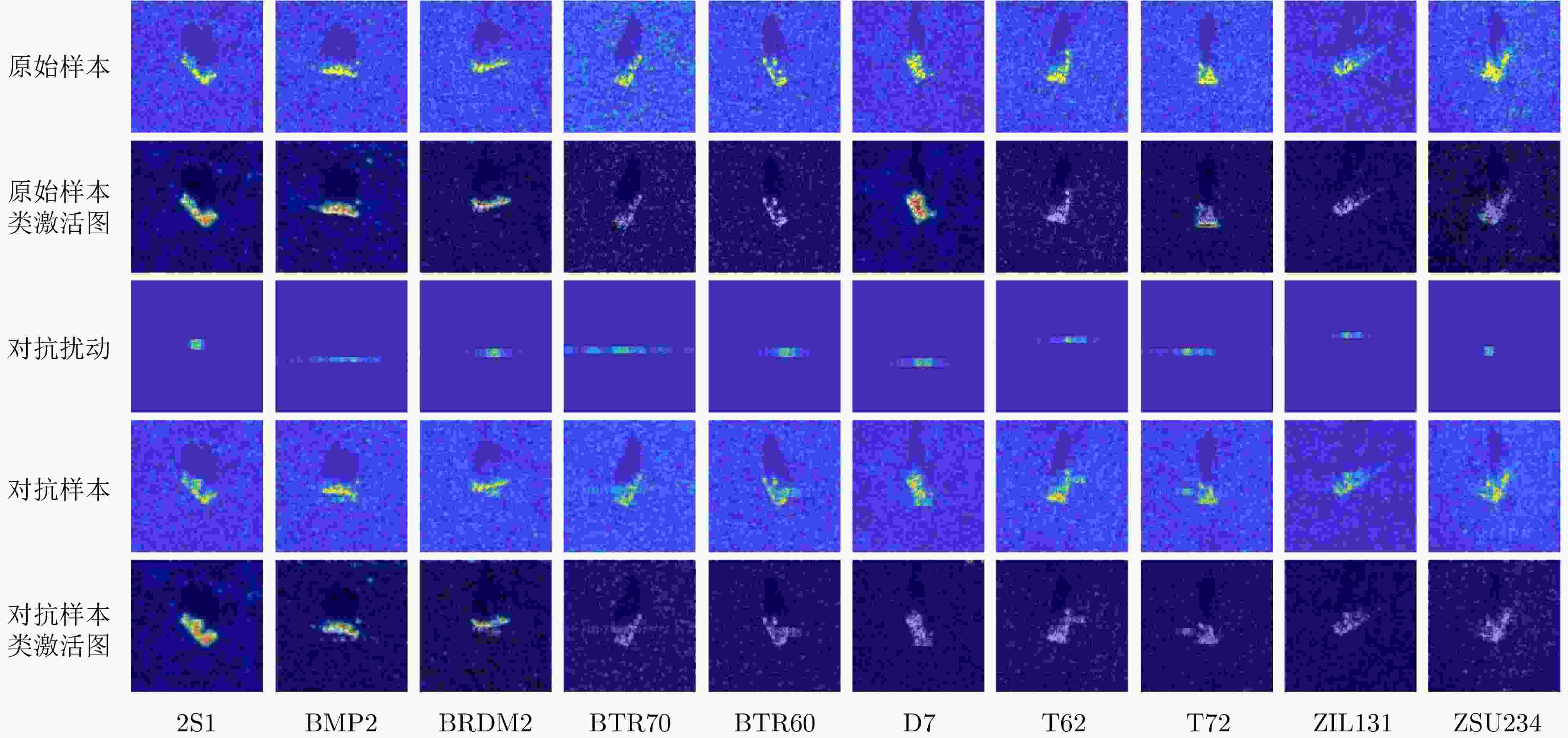
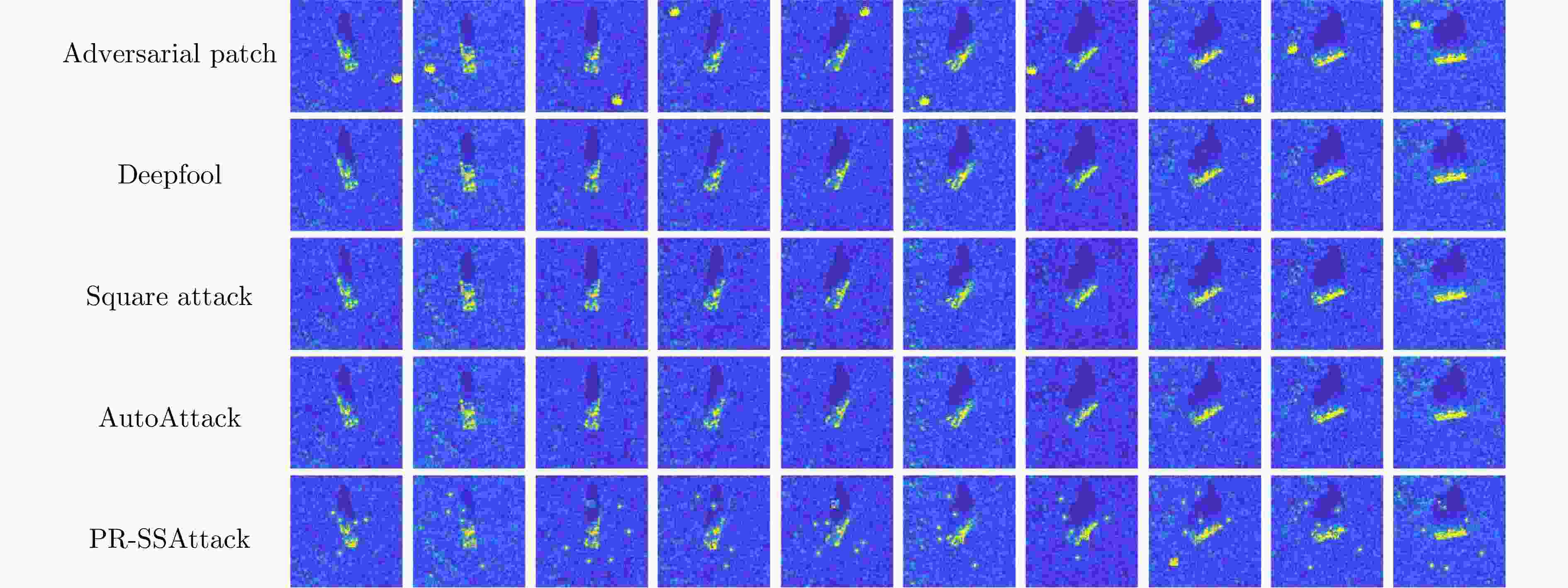
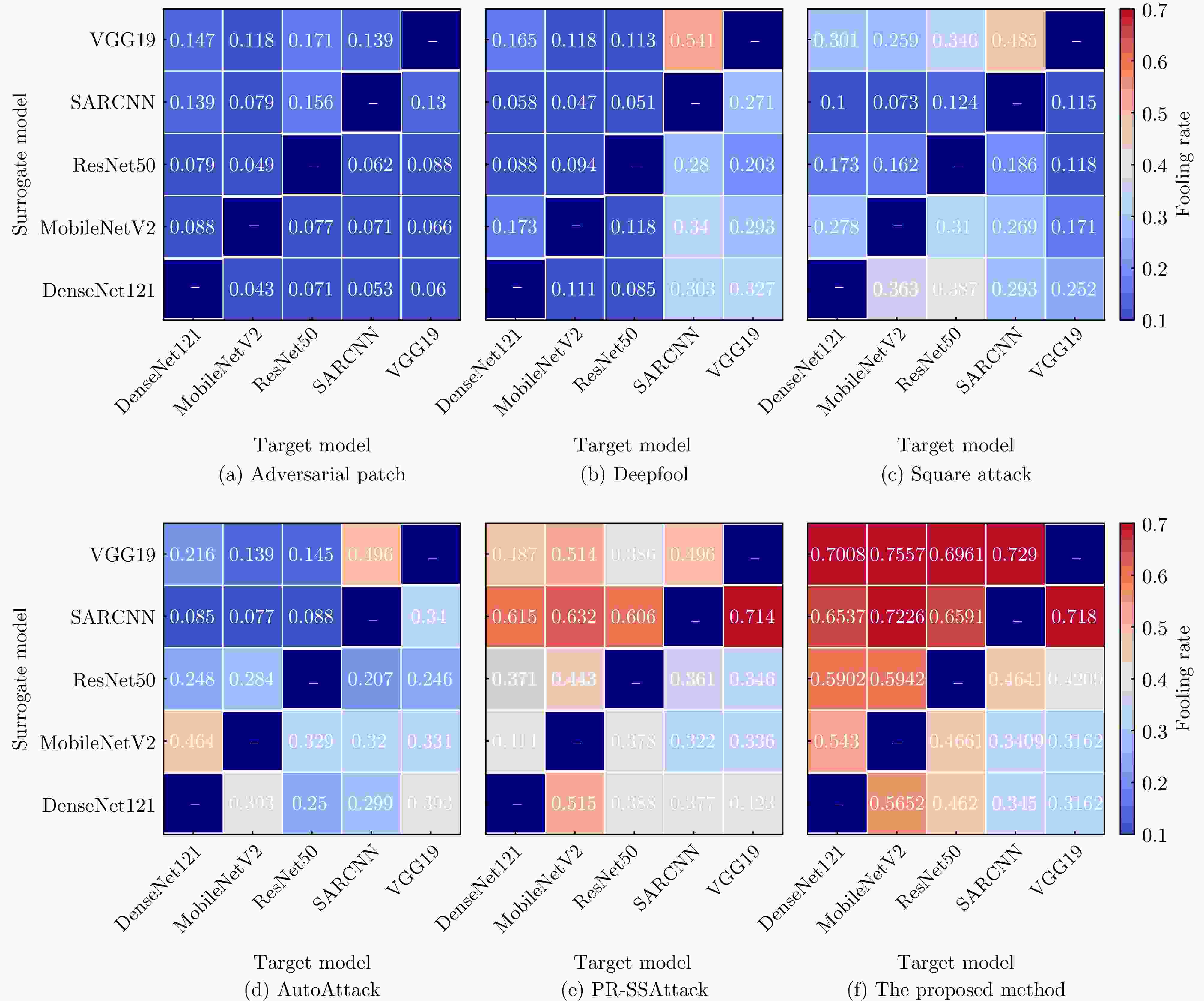
对抗攻击方法 SAR-CNN VGG19 ResNet50 DenseNet121 MobileNetV2 Swin Transformer 平均 Adversarial Patch 11.75 14.10 7.91 7.91 5.77 6.42 8.98 Deepfool 97.44 93.16 96.37 95.30 93.80 93.53 94.93 Square Attack 83.76 91.67 81.62 86.75 89.96 89.09 84.14 AutoAttack 77.56 90.81 96.37 95.51 97.25 99.19 92.78 PR-SSAttack[13] 99.59 94.44 96.51 91.19 88.20 67.07 89.50 所提方法 99.39 94.01 92.20 90.57 93.79 71.31 90.88 表 4 飞机全极化数据集详细信息
Table 4. Aircraft dataset details
标签 类别名 HH HV VH VV 训练集 测试集 训练集 测试集 训练集 测试集 训练集 测试集 0 Cessna_208 699 174 700 174 678 169 700 174 1 King_Air_350i 162 40 163 40 154 38 163 40 2 Kodiak_100 699 174 700 174 678 169 700 174 3 Pilatus_PC_12 162 40 163 40 154 38 163 40 4 T504 1397 349 1399 349 1356 338 1399 349 总数 — 3119 777 3125 777 3020 752 3125 777 表 5 不同极化下MobileNetV2模型的分类精度和攻击成功率(%)
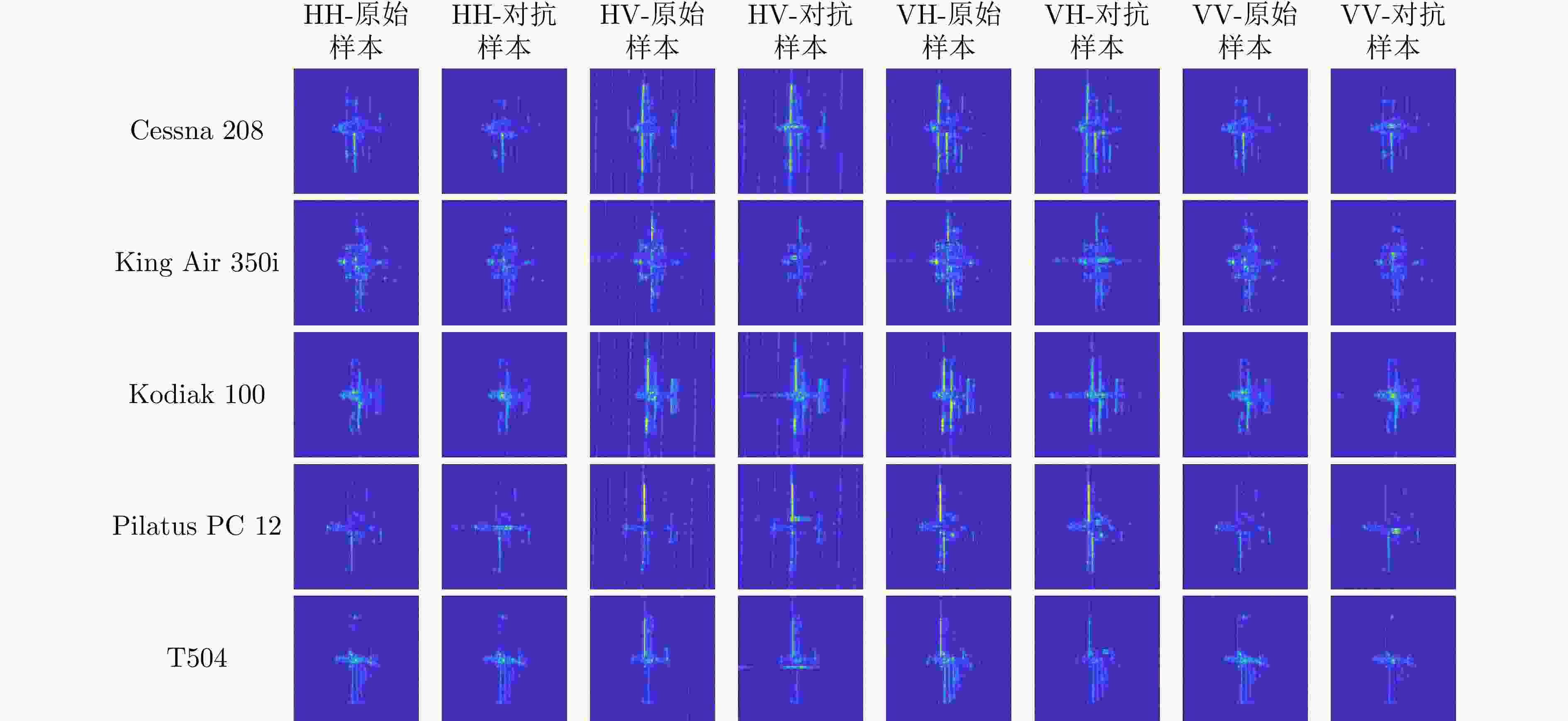
Table 5. Accuracy and fooling rate of MobileNetV2 under different polarizations (%)
极化方式 训练精度 测试精度 攻击成功率 HH 100 96.78 100 HV 100 94.47 99.50 VH 100 89.17 99.50 VV 100 96.53 99.00 -
[1] SZEGEDY C, ZAREMBA W, SUTSKEVER I, et al. Intriguing properties of neural networks[C]. The 2nd International Conference on Learning Representations, Banff, Canada, 2014. doi: 10.48550/arXiv.1312.6199. [2] 陈岳峰, 毛潇锋, 李裕宏, 等. AI安全—对抗样本技术综述与应用[J]. 信息安全研究, 2019, 5(11): 1000–1007. doi: 10.3969/j.issn.2096-1057.2019.11.009.CHEN Yuefeng, MAO Xiaofeng, LI Yuhong, et al. AI security—research and application on adversarial example[J]. Journal of Information Security Research, 2019, 5(11): 1000–1007. doi: 10.3969/j.issn.2096-1057.2019.11.009. [3] GOODFELLOW I J, SHLENS J, and SZEGEDY C. Explaining and harnessing adversarial examples[C]. The 3rd International Conference on Learning Representations, San Diego, USA, 2015. doi: 10.48550/arXiv.1412.6572. [4] CHEN Pinyu, ZHANG Huan, SHARMA Y, et al. ZOO: Zeroth order optimization based black-box attacks to deep neural networks without training substitute models[C]. The 10th ACM Workshop on Artificial Intelligence and Security, Dallas, USA, 2017: 15–26. doi: 10.1145/3128572.3140448. [5] BROWN T B, MANÉ D, ROY A, et al. Adversarial patch[EB/OL]. https://arxiv.org/abs/1712.09665, 2018. [6] DUAN Ranjie, MA Xingjun, WANG Yisen, et al. Adversarial camouflage: Hiding physical-world attacks with natural styles[C]. 2020 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR), Seattle, USA, 2020: 997–1005. doi: 10.1109/CVPR42600.2020.00108. [7] 阮航, 崔家豪, 毛秀华, 等. SAR目标识别对抗攻击综述: 从数字域迈向物理域[J]. 雷达学报(中英文), 2024, 13(6): 1298–1326. doi: 10.12000/JR24142.RUAN Hang, CUI Jiahao, MAO Xiuhua, et al. A survey of adversarial attacks on SAR target recognition: From digital domain to physical domain[J]. Journal of Radars, 2024, 13(6): 1298–1326. doi: 10.12000/JR24142. [8] 万烜申, 刘伟, 牛朝阳, 等. 基于动量迭代快速梯度符号的SAR ATR深度神经网络黑盒攻击算法[J]. 雷达学报(中英文), 2024, 13(3): 714–729. doi: 10.12000/JR23220.WAN Xuanshen, LIU Wei, NIU Chaoyang, et al. Black-box attack algorithm for SAR ATR deep neural networks based on MI-FGSM[J]. Journal of Radars, 2024, 13(3): 714–729. doi: 10.12000/JR23220. [9] ZHOU Jie, PENG Bo, XIE Jianyue, et al. Conditional random field-based adversarial attack against SAR target detection[J]. IEEE Geoscience and Remote Sensing Letters, 2024, 21: 4004505. doi: 10.1109/LGRS.2024.3365788. [10] DUAN Jiale, QIU Linyao, HE Guangjun, et al. A region-adaptive local perturbation-based method for generating adversarial examples in synthetic aperture radar object detection[J]. Remote Sensing, 2024, 16(6): 997. doi: 10.3390/rs16060997. [11] DANG Xunwang, YAN Hua, HU Liping, et al. SAR image adversarial samples generation based on parametric model[C]. 2021 International Conference on Microwave and Millimeter Wave Technology (ICMMT), Nanjing, China, 2021: 1–3. doi: 10.1109/ICMMT52847.2021.9618140. [12] PENG Bowen, PENG Bo, ZHOU Jie, et al. Scattering model guided adversarial examples for SAR target recognition: Attack and defense[J]. IEEE Transactions on Geoscience and Remote Sensing, 2022, 60: 5236217. doi: 10.1109/TGRS.2022.3213305. [13] YE Tian, KANNAN R, PRASANNA V, et al. Realistic scatterer based adversarial attacks on SAR image classifiers[C]. 2023 IEEE International Radar Conference (RADAR), Sydney, Australia, 2023: 1–6. doi: 10.1109/RADAR54928.2023.10371090. [14] ZHOU Junfan, FENG Sijia, SUN Hao, et al. Attributed scattering center guided adversarial attack for DCNN SAR target recognition[J]. IEEE Geoscience and Remote Sensing Letters, 2023, 20: 4001805. doi: 10.1109/LGRS.2023.3235051. [15] ZHANG Fan, YU Yameng, MA Fei, et al. A physically realizable adversarial attack method against SAR target recognition model[J]. IEEE Journal of Selected Topics in Applied Earth Observations and Remote Sensing, 2024, 17: 11943–11957. doi: 10.1109/JSTARS.2024.3420690. [16] LIU Zhe, XIA Weijie, and LEI Yongzhen. SAR-GPA: SAR generation perturbation algorithm[C]. The 3rd International Conference on Advanced Information Science and System, Sanya, China, 2021: 83. doi: 10.1145/3503047.3503136. [17] XIA Weijie, LIU Zhe, and LI Yi. SAR-PeGA: A generation method of adversarial examples for SAR image target recognition network[J]. IEEE Transactions on Aerospace and Electronic Systems, 2023, 59(2): 1910–1920. doi: 10.1109/TAES.2022.3206261. [18] XIE Jianyue, PENG Bo, LU Zhengzhi, et al. MIGAA: A physical adversarial attack method against SAR recognition models[C]. 2024 9th International Conference on Computer and Communication Systems (ICCCS), Xi’an, China, 2024: 309–314. doi: 10.1109/ICCCS61882.2024.10602913. [19] CUI Jiahao, GUO Wang, SHAO Run, et al. Physics-oriented adversarial attacks on SAR image target recognition[C]. The Second Workshop on New Frontiers in Adversarial Machine Learning, Honolulu, USA, 2023. https://advml-frontier.github.io/past/icml2023/#award. [20] LUO Binyan, CAO Hang, CUI Jiahao, et al. SAR-PATT: A physical adversarial attack for SAR image automatic target recognition[J]. Remote Sensing, 2024, 17(1): 21. doi: 10.3390/rs17010021. [21] LIU Wei, WAN Xuanshen, NIU Chaoyang, et al. Template-based universal adversarial attack for synthetic aperture radar automatic target recognition network[J]. IET Radar, Sonar & Navigation, 2025, 19(1): e12691. doi: 10.1049/rsn2.12691. [22] 徐沙, 黄和国, 张夫龙. 反导雷达新进展及有源干扰技术需求分析[J]. 航天电子对抗, 2016, 32(2): 54–57. doi: 10.16328/j.htdz8511.2016.02.015.XU Sha, HUANG Heguo, and ZHANG Fulong. New progress in anti-missile radar and active jamming techniques requirement[J]. Aerospace Electronic Warfare, 2016, 32(2): 54–57. doi: 10.16328/j.htdz8511.2016.02.015. [23] FRANCESCHETTI G, MIGLIACCIO M, RICCIO D, et al. SARAS: A synthetic aperture radar (SAR) raw signal simulator[J]. IEEE Transactions on Geoscience and Remote Sensing, 2002, 30(1): 110–123. doi: 10.1109/36.124221. [24] 张皓宇, 邢世其. SAR有源干扰对抗仿真软件设计与实现[J]. 舰船电子对抗, 2023, 46(6): 102–110, 120. doi: 10.16426/j.cnki.jcdzdk.2023.06.019.ZHANG Haoyu and XING Shiqi. Design and implementation of active jamming countermeasure simulation software to SAR[J]. Shipboard Electronic Countermeasure, 2023, 46(6): 102–110, 120. doi: 10.16426/j.cnki.jcdzdk.2023.06.019. [25] 王雪松, 刘建成, 张文明, 等. 间歇采样转发干扰的数学原理[J]. 中国科学E辑: 信息科学, 2006, 36(8): 891–901. doi: 10.3969/j.issn.1674-7259.2006.08.007.WANG Xuesong, LIU Jiancheng, ZHANG Wenming, et al. Mathematical principles of intermittent sampling repeater jamming[J]. Science in China Ser. E Information Sciences, 2006, 36(8): 891–901. doi: 10.3969/j.issn.1674-7259.2006.08.007. [26] 吴晓芳, 代大海, 王雪松, 等. 基于微动调制的SAR新型有源干扰方法[J]. 电子学报, 2010, 38(4): 954–959.WU Xiaofang, DAI Dahai, WANG Xuesong, et al. A novel method of active jamming for SAR based on micro motion modulation[J]. Acta Electronica Sinica, 2010, 38(4): 954–959. [27] 胡东辉, 吴一戎. 合成孔径雷达散射波干扰研究[J]. 电子学报, 2002, 30(12): 1882–1884. doi: 10.3321/j.issn:0372-2112.2002.12.040.HU Donghui and WU Yirong. The scatter-wave jamming to SAR[J]. Acta Electronica Sinica, 2002, 30(12): 1882–1884. doi: 10.3321/j.issn:0372-2112.2002.12.040. [28] 王宏艳, 降佳伟, 蒲娟, 等. 基于余弦幅度加权的低旁瓣多相位分段调制干扰方法[J]. 系统工程与电子技术, 2021, 43(11): 3185–3193. doi: 10.12305/j.issn.1001-506X.2021.11.18.WANG Hongyan, JIANG Jiawei, PU Juan, et al. Multiple phases sectionalized modulation jamming method with low sidelobe based on cosine amplitude weighting[J]. Systems Engineering and Electronics, 2021, 43(11): 3185–3193. doi: 10.12305/j.issn.1001-506X.2021.11.18. [29] 伊志勇, 王鸿. 复杂电磁环境下雷达有源干扰机的设计与实现[J]. 应用科技, 2017, 44(2): 84–88. doi: 10.11991/yykj.201608013.YI Zhiyong and WANG Hong. Design and implementation of radar active jammer in complex electromagnetic environment[J]. Computing Magazine of the CCF, 2017, 44(2): 84–88. doi: 10.11991/yykj.201608013. [30] 汪丙南, 张帆, 向茂生. 基于混合域的SAR回波快速算法[J]. 电子与信息学报, 2011, 33(3): 690–695. doi: 10.3724/SP.J.1146.2010.00555.WANG Bingnan, ZHANG Fan, and XIANG Maosheng. SAR raw signal fast algorithm in mixed domain[J]. Journal of Electronics & Information Technology, 2011, 33(3): 690–695. doi: 10.3724/SP.J.1146.2010.00555. [31] 金啸宇, 尹嫱, 倪军, 等. 一种基于场景合成和锚点约束的SAR目标检测网络[J]. 南京信息工程大学学报: 自然科学版, 2020, 12(2): 210–215. doi: 10.13878/j.cnki.jnuist.2020.02.008.JIN Xiaoyu, YIN Qiang, NI Jun, et al. SAR target detection network based on scenario synthesis and anchor constraint[J]. Journal of Nanjing University of Information Science and Technology: Natural Science Edition, 2020, 12(2): 210–215. doi: 10.13878/j.cnki.jnuist.2020.02.008. [32] STORN R and PRICE K. Differential evolution—a simple and efficient heuristic for global optimization over continuous spaces[J]. Journal of Global Optimization, 1997, 11(4): 341–359. doi: 10.1023/A:1008202821328. [33] ZHANG Fan, MENG Tianying, XIANG Deliang, et al. Adversarial deception against SAR target recognition network[J]. IEEE Journal of Selected Topics in Applied Earth Observations and Remote Sensing, 2022, 15: 4507–4520. doi: 10.1109/JSTARS.2022.3179171. [34] SIMONYAN K and ZISSERMAN A. Very deep convolutional networks for large-scale image recognition[C]. The 3rd International Conference on Learning Representations, San Diego, USA, 2015. doi: 10.48550/arXiv.1409.1556. [35] HE Kaiming, ZHANG Xiangyu, REN Shaoqing, et al. Deep residual learning for image recognition[C]. 2016 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), Las Vegas, USA, 2016: 770–778. doi: 10.1109/CVPR.2016.90. [36] HUANG Gao, LIU Zhuang, VAN DER MAATEN L, et al. Densely connected convolutional networks[EB/OL]. https://arxiv.org/abs/1608.06993, 2018. [37] MEHTA S and RASTEGARI M. MobileViT: Light-weight, general-purpose, and mobile-friendly vision transformer[C]. The 10th International Conference on Learning Representations, 2022. https://doi.org/10.48550/arXiv.2110.02178. [38] LIU Ze, LIN Yutong, CAO Yue, et al. Swin transformer: Hierarchical vision transformer using shifted windows[C]. 2021 IEEE/CVF International Conference on Computer Vision, Montreal, Canada, 2021: 9992–10002. doi: 10.1109/ICCV48922.2021.00986. [39] MOOSAVI-DEZFOOLI S M, FAWZI A, and FROSSARD P. DeepFool: A simple and accurate method to fool deep neural networks[C]. 2016 IEEE Conference on Computer Vision and Pattern Recognition, Las Vegas, USA, 2016: 2574–2582. doi: 10.1109/CVPR.2016.282. [40] CROCE F and HEIN M. Reliable evaluation of adversarial robustness with an ensemble of diverse parameter-free attacks[C]. The 37th International Conference on Machine Learning, 2020: 2206–2216. https://icml.cc/Conferences/2020. [41] LI Haifeng, HUANG Haikuo, CHEN Li, et al. Adversarial examples for CNN-based SAR image classification: An experience study[J]. IEEE Journal of Selected Topics in Applied Earth Observations and Remote Sensing, 2021, 14: 1333–1347. doi: 10.1109/JSTARS.2020.3038683. -



 作者中心
作者中心 专家审稿
专家审稿 责编办公
责编办公 编辑办公
编辑办公
 下载:
下载: