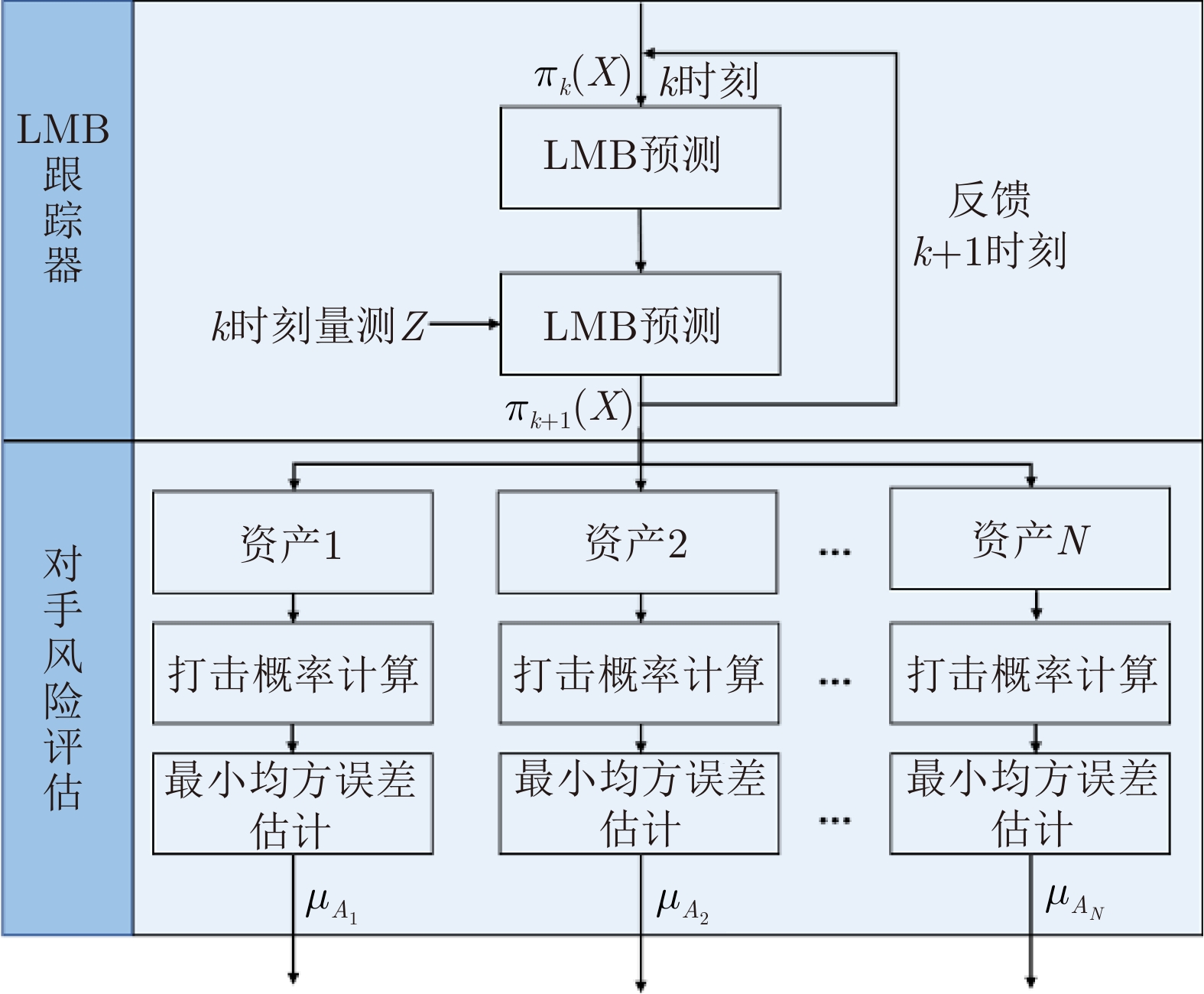
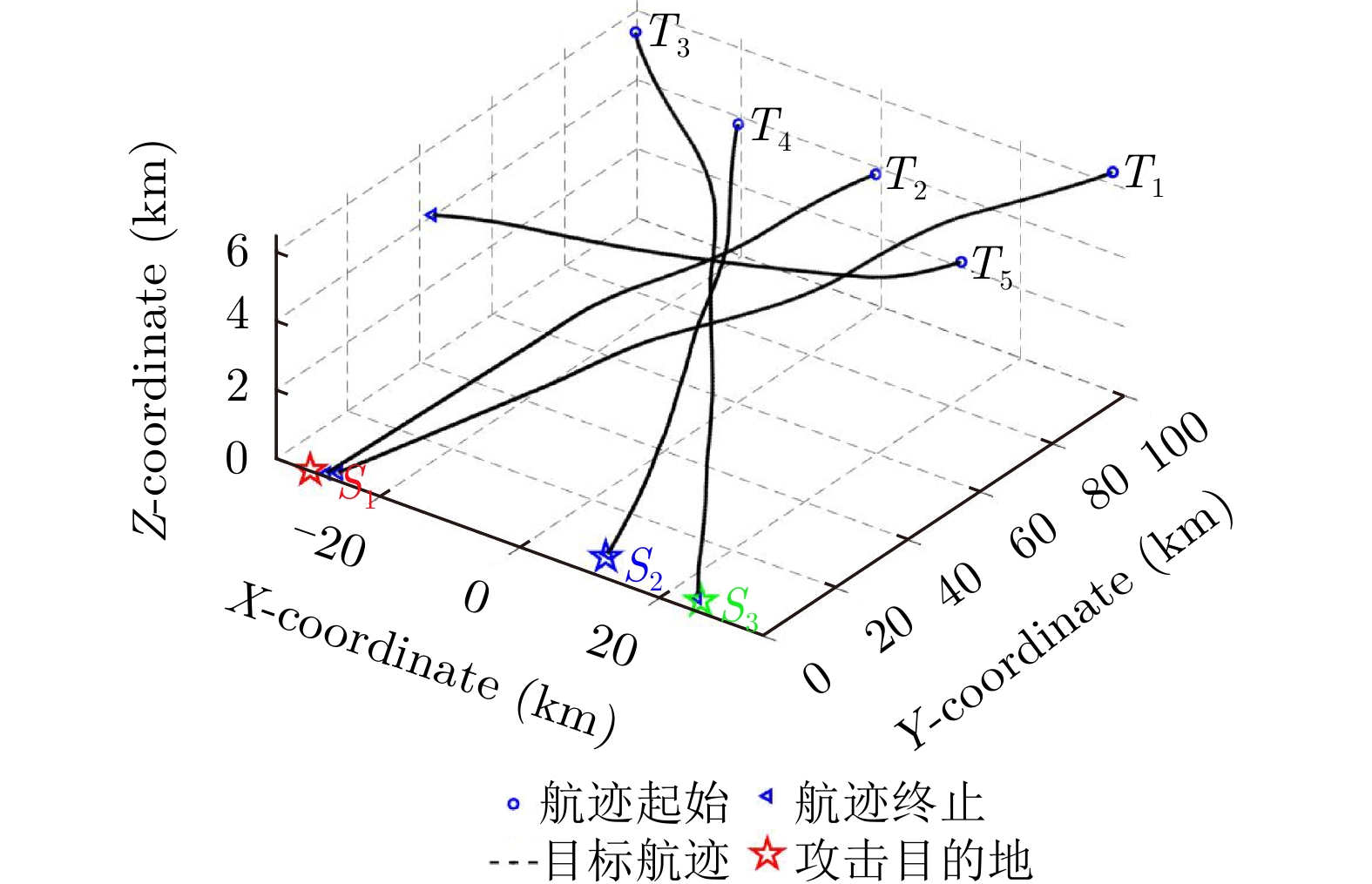
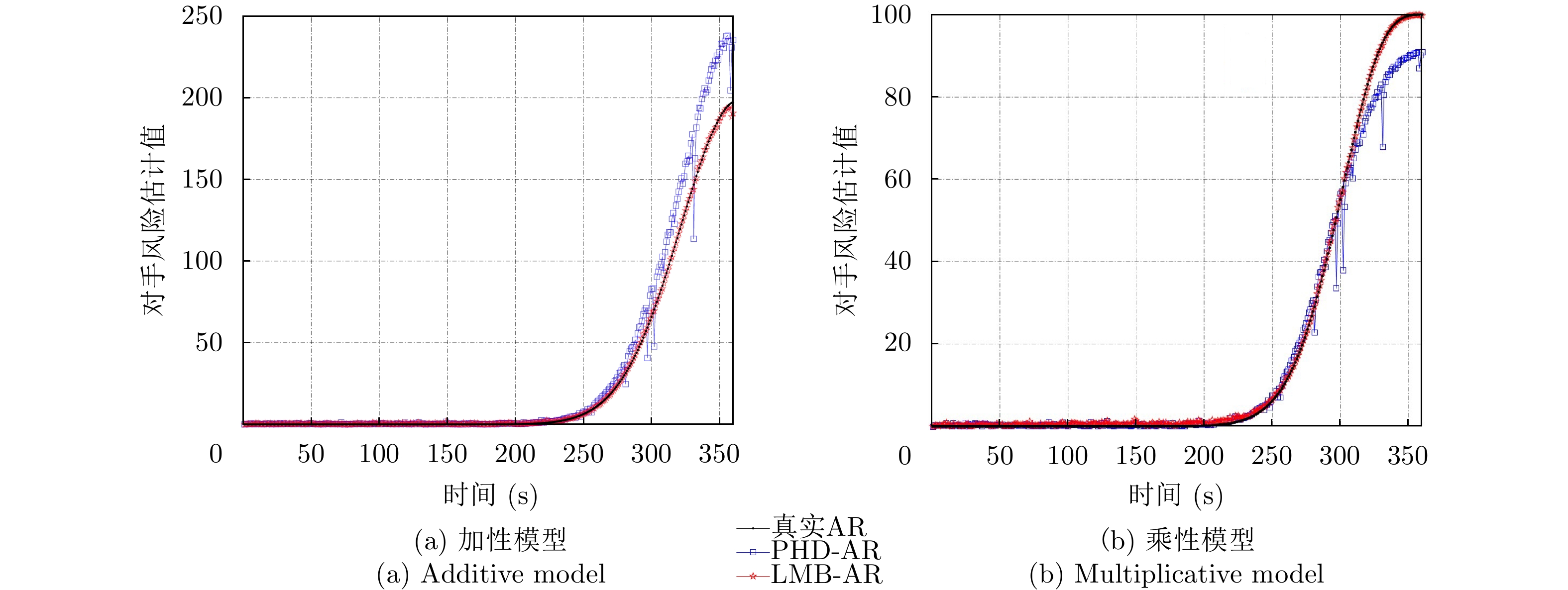
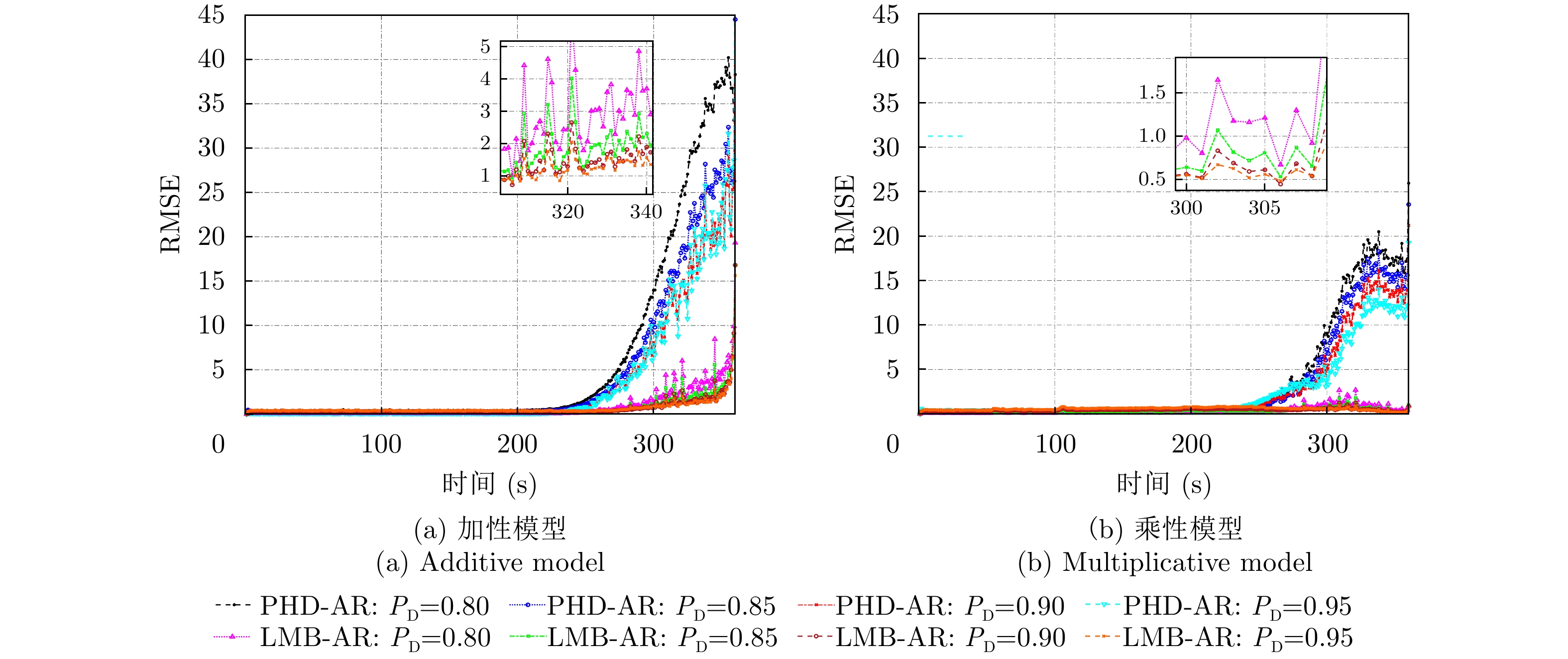
| [1] |
LIU Baoxu, XU Jing, and XU Rongsheng. The study and design of the defence system of the hacker attacks[J]. Computer Engineering and Applications, 2001, 37(8): 1–3, 29. doi: 10.3321/j.issn:1002-8331.2001.08.001 |
| [2] |
WANG Fujun, MEI Wei, WANG Chunping, et al. Prediction of target maneuvering situation based on confrontation information between the enemy and ourselves[J]. Fire Control & Command Control, 2010, 35(9): 152–155. doi: 10.3969/j.issn.1002-0640.2010.09.040 |
| [3] |
LIGGINS II M, HALL D, and LLINAS J. Handbook of Multisensor Data fusion: Theory and Practice[M]. 2nd ed. Boca Raton, USA: CRC Press, 2009: 1–870.
|
| [4] |
GONG Hua, YU Xiaoye, ZHANG Yong, et al. Dynamic threat assessment of air multi-target based on DBN-TOPSIS method[C]. 2021 China Automation Congress, Beijing, China, 2021: 6902–6907.
|
| [5] |
ROY J, PARADIS S, and ALLOUCHE M. Threat evaluation for impact assessment in situation analysis systems[C]. Signal Processing, Sensor Fusion, and Target Recognition XI, Orlando, USA, 2002: 329–341.
|
| [6] |
ERLANDSSON T and NIKLASSON L. Automatic evaluation of air mission routes with respect to combat survival[J]. Information Fusion, 2014, 20: 88–98. doi: 10.1016/j.inffus.2013.12.001 |
| [7] |
TUZLUKOV V. Signal Processing in Radar Systems[M]. Boca Raton, USA: CRC Press, 2013: 1–632.
|
| [8] |
BOLDERHEIJ F. Mission-driven sensor management: Analysis, design, implementation and simulation[D]. [Ph.D. dissertation], Delft University of Technology, 2007.
|
| [9] |
JOHANSSON F. Evaluating the performance of TEWA systems[D]. [Ph.D. dissertation], Örebro University, 2010: 1–177.
|
| [10] |
NARYKOV A, DELANDE E, and CLARK D E. A Formulation of the adversarial risk for multiobject filtering[J]. IEEE Transactions on Aerospace and Electronic Systems, 2021, 57(4): 2082–2092. doi: 10.1109/TAES.2021.3098130 |
| [11] |
LUCAS T W. Damage functions and estimates of fratricide and collateral damage[J]. Naval Research Logistics (NRL), 2003, 50(4): 306–321. doi: 10.1002/nav.10057 |
| [12] |
HOFFMAN J R, SORENSEN E, STELZIG C A, et al. Scientific performance estimation of robustness and threat[C]. Signal Processing, Sensor Fusion, and Target Recognition XI, Orlando, USA, 2002: 248–258.
|
| [13] |
CLARK D E. Stochastic multi-object guidance laws for interception and rendezvous problems[J]. IEEE Transactions on Automatic Control, 2022, 67(3): 1482–1489. doi: 10.1109/TAC.2021.3062559 |
| [14] |
MAHLER R P S. Statistical Multisource-Multitarget Information Fusion[M]. Boston, USA: Artech House, 2007: 1–888.
|
| [15] |
ZHOU Xueqin, LIAO Li, and GAO Feng. Application of Bernoulli filter in single-station passive tracking[J]. Telecommunication Engineering, 2019, 59(4): 419–425. doi: 10.3969/j.issn.1001-893x.2019.04.009 |
| [16] |
MAHLER R P S. Multitarget Bayes filtering via first-order multitarget moments[J]. IEEE Transactions on Aerospace and Electronic Systems, 2003, 39(4): 1152–1178. doi: 10.1109/TAES.2003.1261119 |
| [17] |
VO B T, VO B N, and CANTONI A. Analytic implementations of the cardinalized probability hypothesis density filter[J]. IEEE Transactions on Signal Processing, 2007, 55(7): 3553–3567. doi: 10.1109/TSP.2007.894241 |
| [18] |
|
| [19] |
VO B T, VO B N, and CANTONI A. The cardinality balanced multi-target multi-Bernoulli filter and its implementations[J]. IEEE Transactions on Signal Processing, 2009, 57(2): 409–423. doi: 10.1109/TSP.2008.2007924 |
| [20] |
VO B T and VO B N. Labeled random finite sets and multi-object conjugate priors[J]. IEEE Transactions on Signal Processing, 2013, 61(13): 3460–3475. doi: 10.1109/TSP.2013.2259822 |
| [21] |
VO B N, VO B T, and PHUNG D. Labeled random finite sets and the Bayes multi-target tracking filter[J]. IEEE Transactions on Signal Processing, 2014, 62(24): 6554–6567. doi: 10.1109/TSP.2014.2364014 |
| [22] |
SHIM C, VO B T, VO B N, et al. Linear complexity Gibbs sampling for generalized labeled multi-Bernoulli filtering[J]. IEEE Transactions on Signal Processing, 2023, 71: 1981–1994. doi: 10.1109/TSP.2023.3277220 |
| [23] |
REUTER S, VO B T, VO B N, et al. The labeled multi-Bernoulli filter[J]. IEEE Transactions on Signal Processing, 2014, 62(12): 3246–3260. doi: 10.1109/TSP.2014.2323064 |
| [24] |
LI Suqi, YI Wei, HOSEINNEZHAD R, et al. Multiobject tracking for generic observation model using labeled random finite sets[J]. IEEE Transactions on Signal Processing, 2018, 66(2): 368–383. doi: 10.1109/TSP.2017.2764864 |
| [25] |
LI Suqi, BATTISTELLI G, CHISCI L, et al. Computationally efficient multi-agent multi-object tracking with labeled random finite sets[J]. IEEE Transactions on Signal Processing, 2019, 67(1): 260–275. doi: 10.1109/TSP.2018.2880704 |
| [26] |
LI Suqi, YI Wei, HOSEINNEZHAD R, et al. Robust distributed fusion with labeled random finite sets[J]. IEEE Transactions on Signal Processing, 2018, 66(2): 278–293. doi: 10.1109/TSP.2017.2760286 |
| [27] |
李溯琪. 基于标号随机集的传感器网络分布式融合技术研究[D]. [博士论文], 电子科技大学, 2018: 1–142.
LI Suqi. Labeled random finite set based distributed fusion over sensor network[D]. [Ph.D. dissertation], University of Electronic Science and Technology of China, 2018: 1–142.
|
| [28] |
NGUYEN T T D, VO B N, VO B T, et al. Tracking cells and their lineages via labeled random finite sets[J]. IEEE Transactions on Signal Processing, 2021, 69: 5611–5626. doi: 10.1109/TSP.2021.3111705 |
| [29] |
徐开明, 王佰录, 李溯琪, 等. 低空监视雷达“走-停-走”目标跟踪技术[J]. 雷达学报, 2022, 11(3): 443–458. doi: 10.12000/JR21211XU Kaiming, WANG Bailu, LI Suqi, et al. Move-stop-move target tracking with low-altitude surveillance radars[J]. Journal of Radars, 2022, 11(3): 443–458. doi: 10.12000/JR21211 |
| [30] |
WANG Bailu, LI Suqi, YI Wei, et al. Performance analysis for parallel grouping-based labeled multi-Bernoulli filter[J]. Signal Processing, 2023, 202: 108779. doi: 10.1016/j.sigpro.2022.108779 |
| [31] |
WITKOWSKI M, WHITE G, LOUVIERIS P, et al. High-level information fusion and mission planning in highly anisotropic threat spaces[C]. IEEE 11th International Conference on Information Fusion, Cologne, Germany, 2008: 1–8.
|
| [32] |
NARYKOV A, DELANDE E, CLARK D, et al. Second-order statistics for threat assessment with the PHD filter[C]. Sensor Signal Processing for Defence Conference (SSPD), London, UK, 2017: 1–5.
|
| [33] |
HORREY W J, WICKENS C D, STRAUSS R, et al. Supporting situation assessment through attention guidance and diagnostic aiding: The benefits and costs of display enhancement on judgment skill[J]. Adaptive Perspectives on Human-Technology Interaction: Methods and Models for Cognitive Engineering and Human-Computer Interaction, 2006: 55–70.
|
| [34] |
FANG Fang, HE Jiafan, LI Qingwei, et al. Weapon-target assignment based on improved particle swarm optimization for different allocation criteria[C]. 2021 China Automation Congress (CAC), Beijing, China, 2021: 6628–6633.
|
| [35] |
JOHANSSON F and FALKMAN G. A Bayesian network approach to threat evaluation with application to an air defense scenario[C]. IEEE 11th International Conference on Information Fusion, Cologne, Germany, 2008: 1–7.
|
| [36] |
LITTLE E G and ROGOVA G L. An ontological analysis of threat and vulnerability[C]. IEEE 9th International Conference on Information Fusion, Florence, Italy, 2006: 1–8.
|
| [37] |
GUERRIERO M, SVENSSON L, SVENSSON D, et al. Shooting two birds with two bullets: How to find minimum mean OSPA estimates[C]. IEEE 13th International Conference on Information Fusion, Edinburgh, UK, 2010: 1–8.
|
| [38] |
PAPAGEORGIOU D and RAYKIN M. A risk-based approach to sensor resource management[C]. Advances in Cooperative Control and Optimization. Berlin, Germany: Springer, 2007: 129–144.
|
| [39] |
ANGLEY D, RISTIC B, MORAN W, et al. Search for targets in a risky environment using multi-objective optimisation[J]. IET Radar, Sonar & Navigation, 2019, 13(1): 123–127. doi: 10.1049/iet-rsn.2018.5184 |
| [40] |
DITZEL M, KESTER L, VAN DEN BROEK S, et al. Cross-layer utility-based system optimization[C]. The IEEE 16th International Conference on Information Fusion, Istanbul, Turkey, 2013: 507–514.
|
| [41] |
KATSILIERIS F, DRIESSEN H, and YAROVOY A. Threat-based sensor management for target tracking[J]. IEEE Transactions on Aerospace and Electronic Systems, 2015, 51(4): 2772–2785. doi: 10.1109/TAES.2015.140052 |
| [42] |
BENAVOLI A, RISTIC B, FARINA A, et al. An application of evidential networks to threat assessment[J]. IEEE Transactions on Aerospace and Electronic Systems, 2009, 45(2): 620–639. doi: 10.1109/TAES.2009.5089545 |




 Submit Manuscript
Submit Manuscript Peer Review
Peer Review Editor Work
Editor Work





 DownLoad:
DownLoad: